Topology refers to the way in which the network of computers is connected. Each topology is suited to specific tasks and has its own advantages and disadvantages.
The choice of topology is dependent upon
- type and number of equipment being used
- planned applications and rate of data transfers
- required response times
- cost
There are FOUR major competing topologies
Most networking software support all topologies.
Bus Topology
- all workstations connect to the same cable segment
- commonly used for implementing Ethernet at 10mbps
- the cable is terminated at each end
- wiring is normally done point to point
- a faulty cable or workstation will take the entire LAN down
- two wire, generally implemented using coaxial cable during the 1980's
The bus cable carries the transmitted message along the cable. As the message arrives at each workstation, the workstation computer checks the destination address contained in the message to see if it matches it's own. If the address does not match, the workstation does nothing more.
If the workstation address matches that contained in the message, the workstation processes the message. The message is transmitted along the cable and is visible to all computers connected to that cable.
There are THREE common wiring implementations for bus networks
- 10Base2 (thin-net, CheaperNet) 50-ohm cable using BNC T connectors, cards provide transceiver
- 10Base5 (ThickNet) 50-ohm cable using 15-pin AUI D-type connectors and external transceivers
- 10BaseT (UTP) UTP cable using RJ45 connectors and a wiring centre
The above diagram shows a number of computers connected to a Bus cable, in this case, implemented as Thin Ethernet. Each computer has a network card installed, which directly attaches to the network bus cable via a T-Connector.
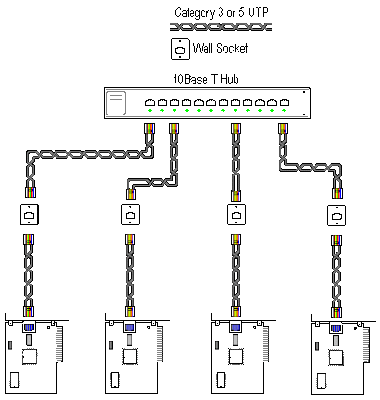
It is becoming common to use 10BaseT (UTP) for implementing Ethernet LANS. Each workstation is wired in star fashion back to a concentrator wiring centre (hub). The hub is a multi-port device supporting up to about 32 ports. One of these ports is connected to a server, or the output of the hub can be connected to other hubs.
Ethernet 802.3: Carrier Sense Multiple Access with Collision Detection (CSMA/CD)
This protocol is commonly used in bus (Ethernet) implementations.
This protocol is commonly used in bus (Ethernet) implementations.
Multiple access refers to the fact that in bus systems, each station has access to the common cable.
Carrier sense refers to the fact that each station listens to see if no other station is transmitting before sending data.
Collision detection refers to the principle of listening to see if other stations are transmitting whilst we are transmitting.
In bus systems, all stations have access to the same cable medium. It is therefore possible that a station may already be transmitting when another station wants to transmit. Rule 1 is that a station must listen to determine if another station is transmitting before initiating a transmission. If the network is busy, then the station must back off and wait a random interval before trying again.
Rule 2 is that a station which is transmitting must monitor the network to see if another station has begun transmission. This is a collision, and if this occurs, both stations must back off and retry after a random time interval. As it takes a finite time for signals to travel down the cable, it is possible for more than one station to think that the network is free and both grab it at the same time.
CSMA/CD models what happens in the real world. People involved in group conversation tend to obey much the same behavior.
Physical Bus Cable Limits
Limitations
- maximum number of trunk segments = 5
- maximum trunk segment length = 607 feet (185 meters)
- maximum network trunk cable = 3035 feet (925 meters)
- maximum number of stations on a trunk segment = 30
- minimum distance between T connectors = 1.5 feet (0.5 meters)
Rules
- each end of the trunk segment is terminated in 50-ohms
- one of the terminators is grounded
- connector splices are kept to a minimum
Cabling
- BNC-T type connectors
10Base5 Thick Ethernet Network layout
Limitations
- maximum number of trunk segments = 5
- maximum trunk segment length = 1640 feet (500 meters)
- maximum network trunk cable = 8200 feet (2500 meters)
- maximum number of stations on a trunk segment = 100
- minimum distance between transceivers = 8 feet (2.5 meters)
- maximum transceiver cable length = 165 feet (50 meters)
Rules
- each end of the trunk segment is terminated in 50-ohm
- one of the terminators is grounded
- connector splices are kept to a minimum
Cabling
- Transceivers 802.3
- 50-ohm cable RG-11
Wiring of the DIX Connector
| Pin | Ethernet | IEEE 802.3 | |
| 1 | Shield | Control-in | Shield |
| 2 | Collision presence+ | Control-in | A |
| 3 | Transmit+ | Data-out | A |
| 4 | Reserved | Data-in | Shield |
| 5 | Receive+ | Data-in | A |
| 6 | Power return | Voltage | common |
| 7 | Reserved | Control-out | A |
| 8 | Reserved | Control-out | Shield |
| 9 | Collision presence- | Control-in | B |
| 10 | Transmit- | Data-out | B |
| 11 | Reserved | Data-out | Shield |
| 12 | Receive- | Data-in | B |
| 13 | Power | Voltage | |
| 14 | Reserved | Voltage | Shield |
| 15 | Reserved | Control-out | B |
| Shell | --- | Protective | Ground |
10Base TUTP Network layout
Limitations
- maximum segment length of 100 Meters
- Hub to Hub or repeater to repeater links limited to 100 Meters
Rules
- star topology
- 4 repeater/5 segment rule of 10Base5 is retained
- only two nodes per segment are allowed
Cabling
- RJ-45 Connectors
- Category 3 UTP minimum, preferably Category 5
Bus Network Topology Summary
| Advantages | Disadvantages |
| Easy to implement | Limits on cable length and Workstation numbers |
| Low Cost | Difficult to isolate network faults |
| | A cable fault affects all workstations |
| | As the number of workstations increase, the speed of the network slows down |
Ring Topology
- workstations connect to the ring
- faulty workstations can be bypassed
- more cabling required than bus
- the connectors used tend to cause a lot of problems
- commonly used to implement token ring at 4 and 16mbps
- four wire, generally STP or UTP
Physical Implementation of ring network
Each workstation is connected back to a Multiple Access Unit (MAU), which supports up to eight workstations. Additional MAU are cascaded to provide greater workstation numbers.
Wiring is performed in a physical star fashion, with cables wired directly from each workstation back to the MAU.
IEEE 802.5 TOKEN RING
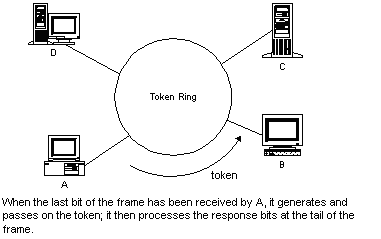
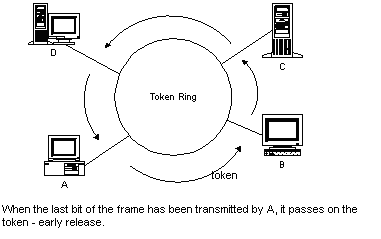
This protocol is widely used in ring networks for controlling station access to the ring. A short message (called a token) is circulated around the ring, being passed from station to station (it originates from a controller or master station which inserts it onto the ring).A station which wants to transmit waits for the token to arrive. When the token arrives, the station changes it from a token to a connector message, and appends its message. This new message is then placed on the outgoing side of the ring.Each station passes on received tokens if they have nothing to transmit. They monitor connector messages to see if the message is addressed to them. If connector messages are addressed to them, they copy the message, modify it to signify its receipt, then send it on around the ring. Connector messages which are not addressed to them are passed directly on to the next station in the ring.When the connector message travels full circle and arrives at the original sending station, it checks the message to see if it's been received. It then discards the message and replaces it with a token.
OR
PHYSICAL RING CABLE LIMITS
Token Ring Network Layout
Limitations
- maximum number of workstations = 96
- maximum number of 8228 MAU's = 12
- maximum patch cable distance between an 8228 MAU and a station (not including 8' adapter cable) = 150 feet (45 meters)
- maximum patch cable distance between two 8228's = 150 feet (45 meters)
- maximum patch cable connecting all 8228's = 400 feet (120 meters)
Rules
- stations are connected into the jacks of the 8228 units
- patch cables interconnect RO to RI for 8228 units.
- the last RO is connected to the first RI to form a ring.
Cable
- patch cables generally type 6 (26 awg) or 1 (22 awg)
- type 1 for lengths > 66 feet (20 meters)
- IBM 8310574 MIC connectors
- alternatively, UTP with RJ45 connectors.
Ring Topology: Summary
| Advantages | Disadvantages |
| Cable failures affect limited users | Costly Wiring |
| Equal access for all users | Difficult Connections |
| Each workstation has full access speed to the ring | Expensive Adaptor Cards |
| As workstation numbers increase performance diminishes slightly | |
Star Topology
- all wiring is done from a central point (the server or hub)
- has the greatest cable lengths of any topology (and thus uses the most amount of cable)
- generally STP or UTP, four wire
Star Topology: Summary
| Advantages | Disadvantages |
| Easy to add new workstations | Hub failure cripples all workstations connected to that hub |
| Centralized control | Hubs are slighty more expensive than thin-Ethernet |
| Centralized network/hub monitoring | |
FDDI Topology
- 100mbps
- normally implemented over fiber optic (fast-Ethernet, UTP)
- dual redundancy built in by use of primary and secondary ring
- automatic bypassing and isolation of faulty nodes
Fiber Distributed Data Inferface
FDDI is based on two counter rotating 100-Mbit/sec token-passing rings. The rings consist of point to point wiring between nodes which repeat the data as it is received.The primary ring is used for data transmission; the secondary is used for data transmission or to back up the primary ring in the event of a link or station failure. FDDI supports a sustained transfer rate of about 80Mbps, a maximum of 1000 connections (500 nodes) and a total distance of 200 kilometers end to end. There is a maximum distance of 2 kilometers between active nodes.
FDDI Station types
There are two main types of stations, class A which attach directly to dual rings; or class B which attach to a station acting as a concentrator.A concentrator is a specialized workstation that attaches to the ring and has multiple ports that allow attachment of other devices in a physical star configuration. These may be cascaded.
Logical Networks versus Physical Networks
A logical network describes how the network operates. A physical network describes how the network has been cabled. It is thus possible to have a physical star, logical bus network. In other words, the network operates as a bus network, but the cabling has been implemented using star topology.